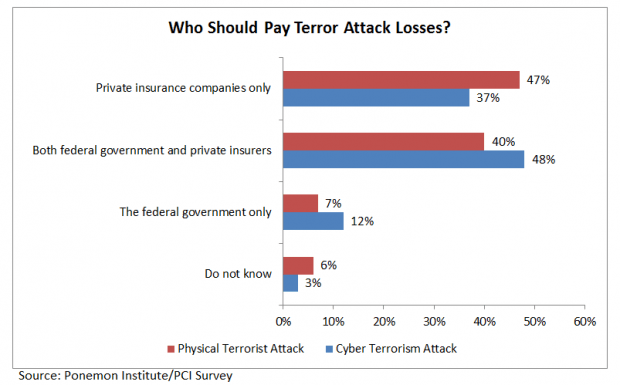
Forty-seven percent of security executives across of a variety of industries believe that private insurance companies alone should pay for worker injuries and property damage in the aftermath of a catastrophic physical terrorist attack, according to new report.
The just-published survey of 622 IT security executives sponsored by the Property Casualty Insurers Association of America and conducted by Ponemon Institute reveals the answer “private insurance companies only” as the top choice of respondents to a multiple-choice question about who should be responsible for these costs. The margin was slim, however, with an alternative choice—”both federal government and private insurance companies”—garnering 40 percent of the responses.
Answering a more direct question about federal terrorism insurance, a clearer majority of 65 percent said they “strongly agree” (33 percent) or “agree” (32 percent) that there should be a federal terror insurance program in place.
The differences in the responses to the two questions may be explained by the fact that some of the security professionals believe the federal government needs to play a bigger role in responding to losses from a “large-scale cyber terrorism attack” than in responding to a physical terror attack. Asked about cyber terror specifically, only 37 percent said private insurance companies alone should respond to losses, while 48 percent saw a dual role for insurers and the federal government.
Security Breaches Short of Catastrophes
In fact, the focus of the study, titled “Cyber Catastrophes: Understanding the Risk and Exposure,” is more on cyber security, with questions about “material security exploits” and “material data breaches” in addition to physical and cyber terror catastrophes.
The stated purpose of the study is to “understand perceptions and beliefs about cyber security insurance as part of an organization’s overall risk management strategy.” On that score, nearly two-thirds (64 percent) of the IT security executives said their firms did not have cyber security insurance in place, but 59 percent said they planned to buy it in 12-24 months.
For the 41 percent who are not budgeting for cyber insurance, reasons include expensive premiums (48 percent), inadequate coverage (43 percent) or perceived coverage under other property/casualty insurance policies (38 percent). Only 9 percent said they are unable to get coverage because of their current risk profile.
Other key findings related to cyber security and risk management include:
- Forty-seven percent of respondents said their companies experienced one or more material security exploits or breaches during the past two years.
- The researchers define a material security exploit as a cyber attack that infiltrates a company’s networks or enterprise systems. A material breach is one that results in loss or theft of thousands of records or leakage of high-value intellectual property.
- The average cost of the exploits and breaches was $9 million.
- The most common security exploit is negligence or mistakes resulting in loss of confidential business information (52 percent). The next most common is cyber attack resulting in theft of consumer information (45 percent).
- While 58 percent said they have a system for monitoring cyber attacks, 32 percent said it is not effectively deployed across the enterprise and 25 percent said it doesn’t function well.
- Only 19 percent said they had well-functioning systems deployed across their enterprises.
Assessing the Potential Impact of Cyber Terror Catastrophes
Asked whether their companies have continuity management plans in place to resume business-as-usual in the event of a cyber catastrophe, more than half (52 percent) said yes. But 40 percent of those indicating that they do have such continuity plans said they were not confident that the plans would work in the event of a large-scale cyber attack.
In contrast, the majority of those who are confident said their companies could be up and running in minutes (31 percent) or hours (45 percent).
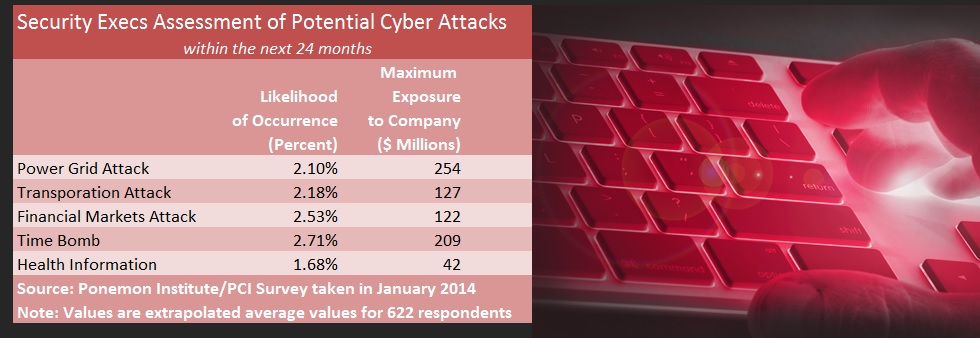
A section of the survey report delves into the security professionals’ assessments of five types of cyber catastrophes, asking the respondents to estimate the probability of each of the attacks occurring in the next 24 months and the maximum economic impact to their companies:
- A terrorist attack to the nation’s power grid (power grid attack).
- A cyber attack against the GPS systems of a major airline (transportation attack).
- A cyber attack against all major brokerage and investment firms (financial markets attack).
- A terror attack against every PC operating system (a time bomb).
- A terror attack against health care provider portals (health information).
The security executives believe the “time bomb” is the most likely of these events. The “power grid attack” would be the most costly, costing their companies $255 million on average, they said.
Respondents’ average responses for all five scenarios are summarized in the accompanying table. The Ponemon report presents a graphical distribution of responses for each of the five scenarios.
Respondent Profile
The survey respondents included a mix of professionals from various industries, with financial services (19 percent), public sector (13 percent), health and pharmaceuticals (12 percent), and retail (9 percent) representing more than half the group. More than half of the survey respondents classified themselves as being at supervisor levels and above, with another 34 percent describing themselves as technicians.
The Ponemon Institute conducted the survey in January 2014.
About Ponemon
Ponemon Institute is dedicated to independent research and education that advances responsible information and privacy management practices within business and government. The Ponemon Institute mission is to conduct high-quality, empirical studies on critical issues affecting the management and security of sensitive information about people and organizations.





















 What Analysts Are Saying About the 2026 P/C Insurance Market
What Analysts Are Saying About the 2026 P/C Insurance Market  20,000 AI Users at Travelers Prep for Innovation 2.0; Claims Call Centers Cut
20,000 AI Users at Travelers Prep for Innovation 2.0; Claims Call Centers Cut  Beazley Agrees to Zurich’s Sweetened £8 Billion Takeover Bid
Beazley Agrees to Zurich’s Sweetened £8 Billion Takeover Bid  Earnings Wrap: With AI-First Mindset, ‘Sky Is the Limit’ at The Hartford
Earnings Wrap: With AI-First Mindset, ‘Sky Is the Limit’ at The Hartford 



